Challenge
The original insider threat tracking process was a manual, rudimentary process that forced analysts to scour through thousands of lines spread across hundreds of spreadsheets. Our team was brought in to investigate how the actual process worked and uncover opportunities for improvement.
What we built
The Solution for Insider Threat Hindrance (SITH) is a Department of Defense project aimed at helping to mitigate and assess insider threat more effectively.
Our team conducted discovery and research sessions with insider threat analysts and stakeholders to identify the true problem, which was a need for a centralized case management system. After defining the problem, we quickly gathered insights from users in usability sessions and built a production-ready MVP (minimum viable product) in six months.
When our team was brought in, the Defense Counterintelligence and Security Agency (DCSA), along with the Directorate for Digital Services (DDS), were still defining the problem space. Our team jumped in and began our Discovery and Framing phase to uncover the insider threat user needs for this project.
Understanding the problem space
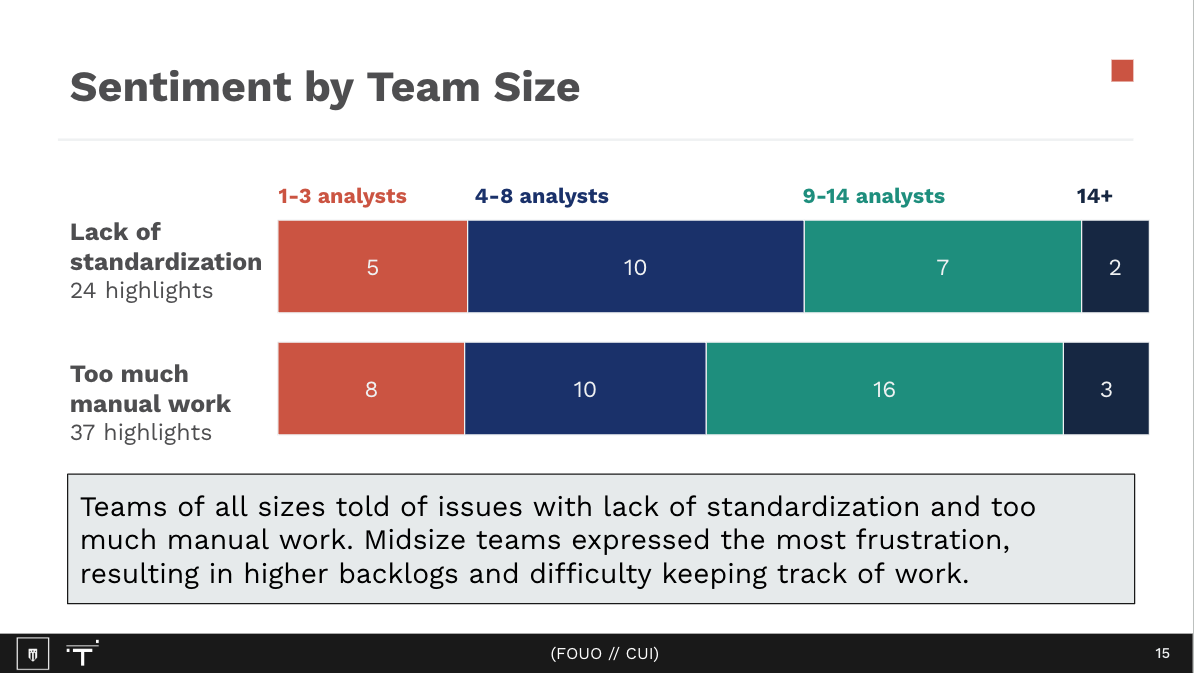
In the first several months, the team conducted over 40 user interviews with individuals and teams in 20 different government agency hubs, which are groups assigned to analyze and mitigate threats at military branches. Each of these interviews was aimed at learning more about the Insider Threat process, along with their wishes and frustrations with the current experiences.
Through these interviews which were conducted mostly virtually, the team learned how multiple insider threat groups keep track of incidents and their surrounding processes and systems.
We organized all of these user interviews in a program called Dovetail, where we were able to analyze specific insights and note their relationships and frequency.